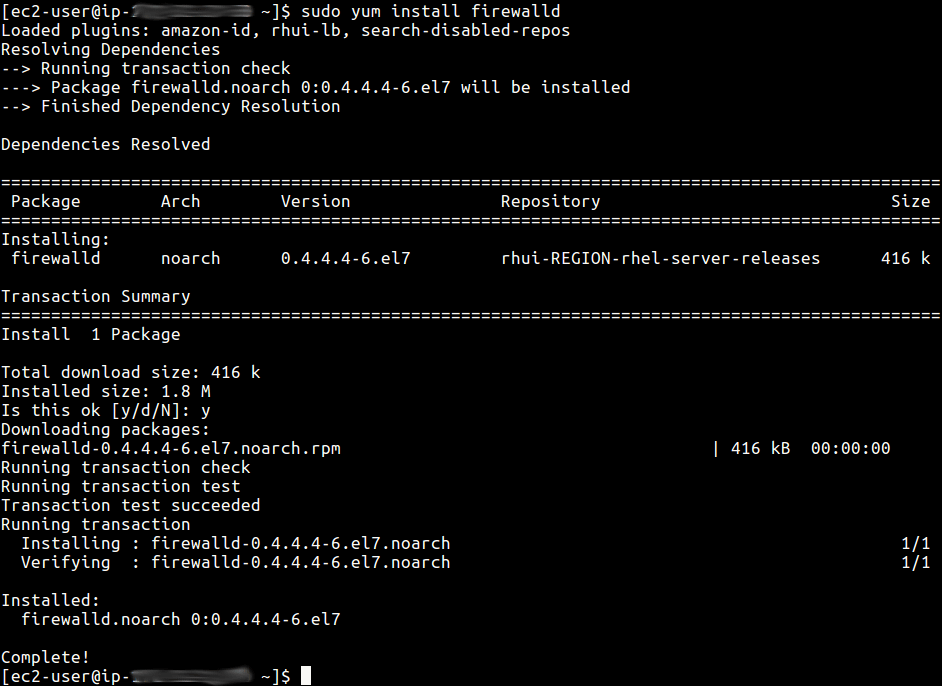
Install Haproxy On Centos 7 Firewalld Open
Mar 17, 2018 - The default installation of Cpanel Server should automatically. It should configure iptables for you, If on CentOS 7, firewalld should be set for you. Note that with firewalld, you can't have a different firewall service like csf running, it will. GPU, Grafana, Graylog, GRUB, Hacking, Hacks, HAProxy, How To. Open firewall port on CentOS 7. Step 1 => install epel repo. If you have multiple ports to allow in Centos 7 FIrewalld then we can use the following command.
Introduction Firewalld is a firewall management solution available for many Linux distributions which acts as a frontend for the iptables packet filtering system provided by the Linux kernel. In this guide, we will cover how to set up a firewall for your server and show you the basics of managing the firewall with the firewall-cmd administrative tool (if you'd rather use iptables with CentOS, follow ). Note: There is a chance that you may be working with a newer version of firewalld than was available at the time of this writing, or that your server was set up slightly differently than the example server used throughout this guide. Thus, the behavior of some of the commands explained in this guide may vary depending on your specific configuration. Basic Concepts in Firewalld Before we begin talking about how to actually use the firewall-cmd utility to manage your firewall configuration, we should get familiar with a few basic concepts that the tool introduces. Zones The firewalld daemon manages groups of rules using entities called 'zones'.
Watch online and download Temptation drama in high quality. Various formats from 240p to 720p HD (or even 1080p). HTML5 available for mobile devices. Theatre korea terbaru ini berjudul Kordramas drama korea cruel temptation subtitle indonesia.play ini merupakan remake dari dorama jepang yang berjudul Kordramas drama korea cruel temptation subtitle indonesia.dilemma korea Kordramas drama korea cruel temptation subtitle indonesia crisis ini anda bisa download di Ezonekorea.com. Watch ' Temptation of Wife ' with our fast and smooth mobile player. Cruel Temptation, Wife's Revenge, Wife's Temptation. You can subtitle on Viki and be part. Cruel Temptation Sub Indo. [Site_Name] can use to contact you, including your full name, telephone number, physical address and e-mail address. Drama korea cruel temptation di indosiar bahubali 3 bahasa indoneaia bad sister2015 full movie sub indo aquaman semi jepang indoxxi 2018 layarkaca21 negeri 5 menara kungfu panda 4 full movie urwahakani red sword 2012 benjamin s tarzan marriage not dating ep 12 subtitle indonesia aksa7 teman tapi menikah 2018 magic tour pange heart prosecutor. Cruel temptation sub indo full.
Zones are basically sets of rules dictating what traffic should be allowed depending on the level of trust you have in the networks your computer is connected to. Network interfaces are assigned a zone to dictate the behavior that the firewall should allow. For computers that might move between networks frequently (like laptops), this kind of flexibility provides a good method of changing your rules depending on your environment. You may have strict rules in place prohibiting most traffic when operating on a public WiFi network, while allowing more relaxed restrictions when connected to your home network. For a server, these zones are not as immediately important because the network environment rarely, if ever, changes.
Regardless of how dynamic your network environment may be, it is still useful to be familiar with the general idea behind each of the predefined zones for firewalld. In order from least trusted to most trusted, the predefined zones within firewalld are: • drop: The lowest level of trust. All incoming connections are dropped without reply and only outgoing connections are possible. • block: Similar to the above, but instead of simply dropping connections, incoming requests are rejected with an icmp-host-prohibited or icmp6-adm-prohibited message. • public: Represents public, untrusted networks. You don't trust other computers but may allow selected incoming connections on a case-by-case basis. • external: External networks in the event that you are using the firewall as your gateway.
It is configured for NAT masquerading so that your internal network remains private but reachable. • internal: The other side of the external zone, used for the internal portion of a gateway. The computers are fairly trustworthy and some additional services are available. Download guitar hero pc 10 download. • dmz: Used for computers located in a DMZ (isolated computers that will not have access to the rest of your network).
Only certain incoming connections are allowed. • work: Used for work machines. Trust most of the computers in the network. A few more services might be allowed. • home: A home environment. It generally implies that you trust most of the other computers and that a few more services will be accepted.
• trusted: Trust all of the machines in the network. The most open of the available options and should be used sparingly. To use the firewall, we can create rules and alter the properties of our zones and then assign our network interfaces to whichever zones are most appropriate.
Rule Permanence In firewalld, rules can be designated as either permanent or immediate. If a rule is added or modified, by default, the behavior of the currently running firewall is modified. At the next boot, the old rules will be reverted. Most firewall-cmd operations can take the --permanent flag to indicate that the non-ephemeral firewall should be targeted. This will affect the rule set that is reloaded upon boot.
This separation means that you can test rules in your active firewall instance and then reload if there are problems. You can also use the --permanent flag to build out an entire set of rules over time that will all be applied at once when the reload command is issued.