Hack WiFi Wireshark
Wireshark Hacking tutorial: Wireshark is a complete package filled with network analysis tools. Wireshark is not only a packet sniffer but also a packet analyzer, password hacker, and a firewall. It can also detect any denial of service attack on your network and can identify possible hacker.
Jan 24, 2016 - Meet Wireshark. Wireshark is a packet sniffing tool, a network packet analyzer. Pick the network of interest (probably WiFi). Steps to using Wireshark and Kali Linux. 1 Start Kali Linux and go to Application–>Sniffing spoofing–>Network Sniffers–>wireshark 2 After Wireshark starts click on interface and choose the interface you want to use such as Ethernet or wireless. 3 Wireshark will begin to show all the data that it being transmitted on the network.
Wireshark is also used sometimes as a tool to detect if anyone is spying on you. In this Wireshark Hacking tutorial, we will discuss how Wireshark can be used in multiple ways. As already discussed, Wireshark can be used to capture and detect passwords as well as to secure your network from outside intruders.
ARTeam UFD Password Revealer v1.0: potassium: Reversing. Armageddon is an Educational 'Armadillo' unpacking tool designed specifically for testing Unpackmes' using the many protection features available in versions 4.  Armageddon is an Armadillo unpacking tool designed specifically to deal with the many protection features available in versions 3.78 thru 5.40. This tutorial explains underhood. Tutorials [ Download ARTeam Tutorials! Date, Monday 18 February 2008 - 15:35:03. Downloads, 16728. Armageddon V1 8 By Arteam Tutorial. Continued patching at runtime & unpacking armadillo standard protection IAT-Tutorials ARTeam Unpacking Armadillo 5.xx. Download free Armageddon V1.8 By Arteam. 9/8/2016 0 Comments. ARTeam Armageddon v1.8(穿山甲脱壳机) 下载 Eddy 发布于2009-12-11 9:50:24 分类.
Armageddon is an Armadillo unpacking tool designed specifically to deal with the many protection features available in versions 3.78 thru 5.40. This tutorial explains underhood. Tutorials [ Download ARTeam Tutorials! Date, Monday 18 February 2008 - 15:35:03. Downloads, 16728. Armageddon V1 8 By Arteam Tutorial. Continued patching at runtime & unpacking armadillo standard protection IAT-Tutorials ARTeam Unpacking Armadillo 5.xx. Download free Armageddon V1.8 By Arteam. 9/8/2016 0 Comments. ARTeam Armageddon v1.8(穿山甲脱壳机) 下载 Eddy 发布于2009-12-11 9:50:24 分类.
So lets start with our Wireshark tutorial. Installing Wireshark: Wireshark is available for free of cost. You can download Wireshark from its official website by clicking. Fir Linux or Ubuntu users, you can find Wireshark packages on the above link of its. After Downloading Wireshark, install it in your system and launch the application. Wireshark Hacking tutorial: Step 1: Capturing Packets: First of all, we will learn to capture packets from Wireshark. After downloading and installing Wireshark, launch the application.
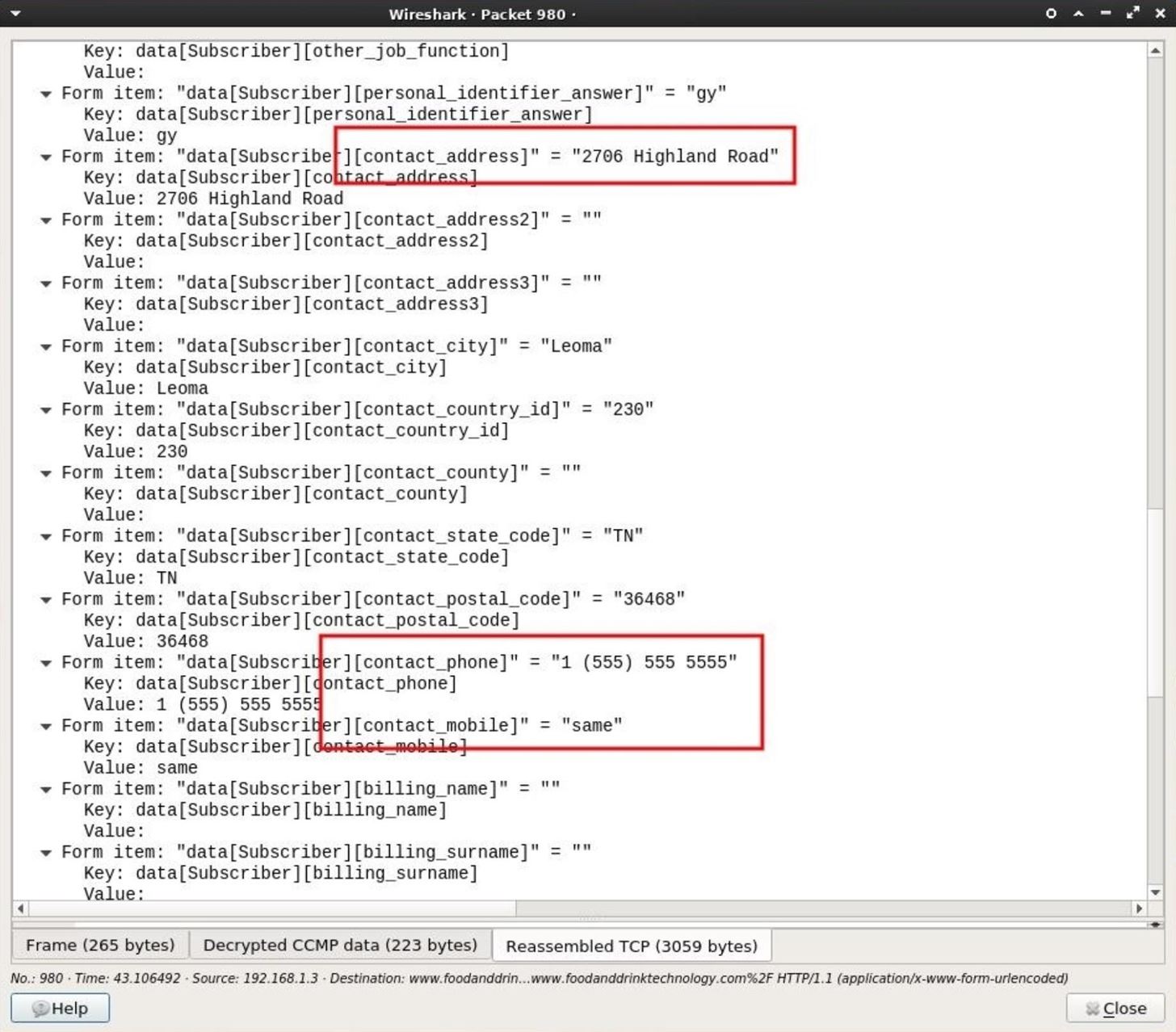
Click the name of an Interface on then Interface list as shown below. Interface list contains your network adapters. If you are connected to a WiFi then select a Wireless Lan Adapter. Wireshark Hacking tutorial After selecting an Interface name, you can see the packets starting to show on your screen.
These packets are being captured by Wireshark in real-time. You can stop packet capturing by clicking on the Stop button( A big Red Square button on the top left corner). Wireshark Hacking tutorial These packets are being captured from your network device. That means that these packets belongs to you and are coming or going out of your system. To capture the packets of other users connected on your Wireless network, enable promiscuous mode on your capture options. Note: You can also see different color coding on your capture packets. These packets are color coded by default.
For example: green is TCP traffic, dark blue is DNS traffic, light blue is UDP traffic, and black is TCP packets with problems. You can also add your custom color code by editing coloring mode in menu. You can save these captured packets for later use. To save a packet, click on File and go to Export Packet Dissections. To open a Packet file, go to the main page and click on open. Step 2: Filtering Packets: Filtering is used to identify a specific packet.
For example, you can filter a traffic received by your browser or from an application. You can also filter packets going through protocols such as DNS, HTTP or TCP. Wireshark Hacking tutorial You can also right-click on a packet and select follow TCP stream. This will automatically add a filter of that packet and Wireshark will show all the packets related to it. Step 3: Inspecting Packets Inspecting a packet helps you to analyze its details. This will let you know the origin of the packet and other details. To do so, click on a packet to select it and its details will be shown.
 The Battlefield 2142 Northern Strike booster pack maps and content are now FREE to play for everyone! Fixes in v1.51: Added extra account security fixes Added fix for nVidia drivers to solve tinitus visual effect Hit detection bug fix: Changed so that latency compensation history takes correct stored positions from buffer Updated as_titan_wake.tweak to allow for two attack choppers instead of the one previously allowed New Features in v1.51: Added Operation Blue Pearl by Bjorn Sundell with special thanks to Jason Brice for lightmaps and finishing Added Yellow Knife, Molokai and Strike at Karkand 2142 maps made by Jason Brice Added support for the.
The Battlefield 2142 Northern Strike booster pack maps and content are now FREE to play for everyone! Fixes in v1.51: Added extra account security fixes Added fix for nVidia drivers to solve tinitus visual effect Hit detection bug fix: Changed so that latency compensation history takes correct stored positions from buffer Updated as_titan_wake.tweak to allow for two attack choppers instead of the one previously allowed New Features in v1.51: Added Operation Blue Pearl by Bjorn Sundell with special thanks to Jason Brice for lightmaps and finishing Added Yellow Knife, Molokai and Strike at Karkand 2142 maps made by Jason Brice Added support for the.
Wireshark Hacking tutorial Right-click on any packet that looks important and select filter. This will show you all the related packets that have been captured.
This list and resource sprung to life when we organized an online poll way back in 2013 that was very well received and the below are the recommended tools that you all voted as the ‘Top Ten List of Hacking Tools’. We’ve organized this list by including information and links to the specific tools with additional information pertaining to the individual tool which we hope will help you. Whilst this list is touted as a “Top Ten” it is definitely a virtually impossible to list only ten “best tools” because, of course, it is very much a subjective choice and decision to select which tools make this list. If you’re not sure where to start then we’d recommend that you take a look at our index of hacking software tools that includes tools from the following hacking/ pentesting categories. The History of “Hacking Tools” within IT Security Traditionally, the perception is that Chinese state hackers (PLA Unit 61398) take stock tools (like the ones listed within our directory) whilst the Russians and Israelis (Unit 8200) have the reputation of building their own customized tools. Tools are what’s needed to get the job done.